Cloud Security Assessments Services
Cloud Security Assessments Services
In an era where cloud computing is integral to business operations, ensuring the security of your cloud services and infrastructure is paramount. Our Cloud Security Assessments Services provide a comprehensive evaluation of your cloud environment to identify vulnerabilities, assess compliance with organizational and regulatory requirements, and implement robust security measures. Whether you’re migrating to the cloud, optimizing your existing cloud infrastructure, or seeking to enhance your cloud security posture, our expert assessments ensure that your cloud assets are secure, resilient, and aligned with your business objectives.
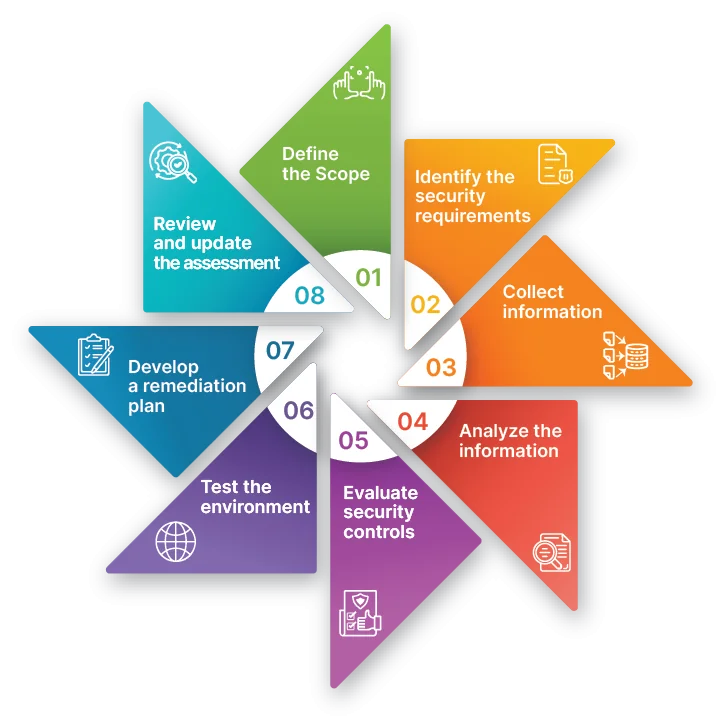
Our Cloud Security Assessments Services are designed to meticulously evaluate the security posture of your cloud services and infrastructure. We analyze your cloud architecture, configurations, policies, and practices to identify potential security gaps and vulnerabilities. By leveraging industry best practices and advanced security frameworks, we help you strengthen your cloud defenses, ensure compliance with relevant regulations, and protect your critical data and applications from evolving cyber threats. Our tailored assessments provide actionable insights and strategic recommendations to enhance the security and efficiency of your cloud environment.
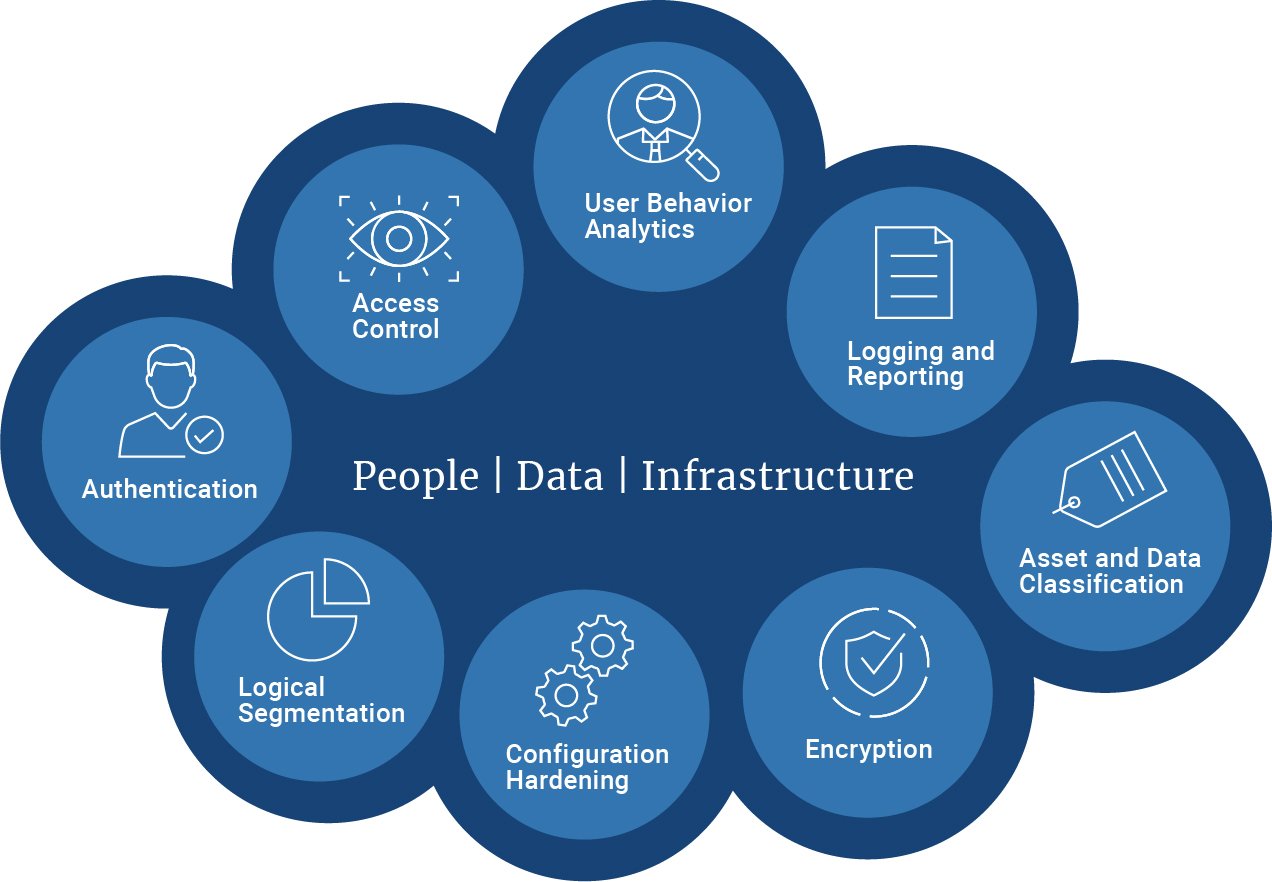
Comprehensive Cloud Security Evaluation:
- Architecture Review: Assess the design and architecture of your cloud infrastructure to ensure it follows security best practices and is resilient against potential threats.
- Configuration Assessment: Examine cloud configurations for services like AWS, Azure, Google Cloud, and others to identify misconfigurations and enforce secure settings.
- Access Control Analysis: Evaluate identity and access management (IAM) policies to ensure that permissions are appropriately assigned and follow the principle of least privilege.
Vulnerability Identification and Risk Assessment:
- Vulnerability Scanning: Utilize advanced scanning tools to detect vulnerabilities in your cloud environment, including unpatched systems, insecure APIs, and exposed services.
- Risk Assessment: Analyze identified vulnerabilities to determine their potential impact and likelihood, prioritizing risks based on severity to guide remediation efforts.
Compliance and Regulatory Alignment:
- Regulatory Compliance Checks: Ensure your cloud infrastructure complies with relevant regulations and standards such as GDPR, HIPAA, PCI DSS, ISO/IEC 27001, and industry-specific guidelines.
- Policy Review and Development: Assess existing security policies and develop or update them to align with regulatory requirements and industry best practices.
Data Protection and Encryption:
- Data Security Evaluation: Examine data storage and transmission practices to ensure robust encryption and protection of sensitive information both at rest and in transit.
- Encryption Key Management: Assess and optimize encryption key management processes to safeguard cryptographic keys against unauthorized access and breaches.
Threat Detection and Incident Response:
- Security Monitoring Review: Evaluate the effectiveness of your cloud security monitoring tools and processes, ensuring timely detection and response to security incidents.
- Incident Response Planning: Develop and enhance incident response plans tailored to your cloud environment, ensuring swift and effective mitigation of security breaches.
Network Security Assessment:
- Network Segmentation Analysis: Assess network segmentation and firewall configurations to prevent lateral movement of threats within your cloud infrastructure.
- Secure Connectivity: Evaluate the security of connectivity between on-premises systems and cloud environments, including VPNs, direct connections, and hybrid setups.
Third-Party and Vendor Risk Management:
- Vendor Security Assessment: Evaluate the security practices of third-party vendors and service providers integrated with your cloud infrastructure to ensure they meet your security standards.
- Contractual Security Requirements: Develop and enforce security requirements within vendor contracts to mitigate risks associated with third-party relationships.
Continuous Improvement and Optimization:
- Security Posture Monitoring: Implement continuous monitoring solutions to maintain visibility into your cloud environment and adapt to evolving threats.
- Performance Metrics and Reporting: Define and track key performance indicators (KPIs) to measure the effectiveness of your cloud security initiatives and identify areas for improvement.
Enhanced Security Posture:
- Proactive Threat Mitigation: Identify and address security vulnerabilities before they can be exploited by malicious actors, reducing the risk of data breaches and cyber incidents.
- Comprehensive Protection: Implement layered security measures that provide robust protection for your cloud infrastructure and sensitive data.
Regulatory Compliance:
- Avoid Penalties: Ensure adherence to relevant data protection and cybersecurity regulations, avoiding hefty fines and legal repercussions associated with non-compliance.
- Audit Readiness: Prepare for regulatory audits with thorough documentation and evidence of your cloud security practices and compliance status.
Operational Efficiency:
- Streamlined Processes: Optimize cloud security processes to enhance operational efficiency, reduce complexity, and ensure consistent security practices across your organization.
- Resource Optimization: Allocate security resources effectively by focusing on high-priority risks and critical vulnerabilities aligned with your business objectives.
Risk Mitigation:
- Reduced Risk Exposure: Minimize the likelihood and impact of cyber threats through effective risk management and mitigation strategies tailored to your cloud environment.
- Business Continuity: Ensure uninterrupted operations with robust incident response and disaster recovery plans integrated into your cloud architecture.
Increased Customer Trust:
- Build Credibility: Demonstrate your commitment to cloud security, fostering trust and confidence among customers, partners, and stakeholders.
- Competitive Advantage: Differentiate your organization from competitors by showcasing superior cloud security measures and compliance with industry standards.
Cost Savings:
- Reduced Remediation Costs: Address security vulnerabilities early in the cloud lifecycle, avoiding the high costs associated with post-incident remediation and data breaches.
- Efficiency Gains: Achieve cost savings by optimizing cloud security processes and reducing redundancies through standardized practices.
Use Cases:
- Financial Services:
- Protect sensitive financial data and transactions in the cloud, ensuring compliance with industry-specific cybersecurity regulations and safeguarding customer trust.
- Healthcare Organizations:
- Safeguard patient information and medical records stored in the cloud, complying with healthcare data protection laws and preventing unauthorized access.
- Government Agencies:
- Secure classified and sensitive government data in cloud environments, maintaining national security and public trust through rigorous security assessments.
- E-Commerce Platforms:
- Ensure the security of customer data and transaction information in the cloud, enhancing trust and reducing the risk of data breaches in online operations.
- Telecommunications Companies:
- Protect communication networks and customer data hosted in the cloud, maintaining reliable and trusted service delivery through comprehensive security evaluations.
- Educational Institutions:
- Safeguard academic records and personal information of students and staff stored in the cloud, ensuring compliance with data protection standards and preventing unauthorized access.
- Manufacturing Firms:
- Protect intellectual property and operational technologies hosted in the cloud, ensuring business continuity and maintaining competitive advantage through robust security measures.
- Retailers and Merchants:
- Secure point-of-sale (POS) systems and customer data in cloud environments to prevent data breaches and maintain compliance with privacy laws.
