Cyber Security Maturity Assessment Services
Cyber Security Maturity Assessment Services
In an increasingly complex digital landscape, understanding and enhancing the maturity of your organization’s cybersecurity practices is essential for safeguarding critical assets and ensuring resilience against evolving threats. Our Cyber Security Maturity Assessment Services provide a comprehensive evaluation of your current cybersecurity posture, identifying strengths and areas for improvement. By assessing the maturity of your cybersecurity practices and processes, we help you develop a strategic roadmap to advance your security capabilities, align with industry best practices, and achieve robust protection against cyber threats.
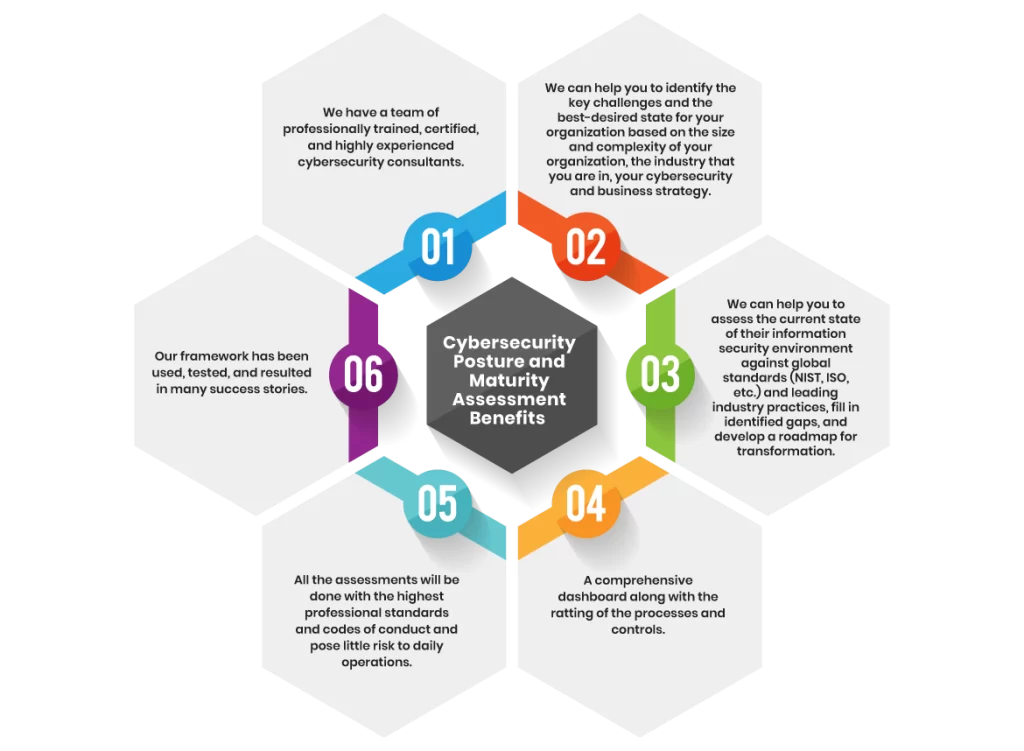
Our Cyber Security Maturity Assessment Services are designed to evaluate the effectiveness and sophistication of your organization’s cybersecurity practices and processes. We utilize established maturity models, such as the NIST Cybersecurity Framework (CSF) and the Capability Maturity Model Integration (CMMI), to benchmark your current security posture against industry standards. This assessment provides actionable insights into how mature your cybersecurity initiatives are, highlights gaps, and offers strategic recommendations to elevate your security maturity level. Whether you are seeking to enhance your existing security measures, prepare for regulatory compliance, or build a foundation for advanced cybersecurity practices, our maturity assessments offer the guidance and expertise needed to achieve your security objectives.

Comprehensive Maturity Evaluation:
- Framework Alignment: Assess your cybersecurity practices against established frameworks such as NIST CSF, ISO/IEC 27001, and CMMI to determine your maturity level.
- Process Review: Examine key cybersecurity processes, including risk management, incident response, asset management, and access control, to evaluate their effectiveness and maturity.
- Technology Assessment: Evaluate the deployment and integration of cybersecurity technologies, ensuring they support your security objectives and mature practices.
Gap Analysis:
- Current vs. Desired State: Identify discrepancies between your current cybersecurity practices and the desired maturity level based on industry standards.
- Prioritization of Gaps: Prioritize identified gaps based on their impact on your overall security posture and business objectives.
Risk Assessment:
- Threat and Vulnerability Identification: Identify potential threats and vulnerabilities that could impact your organization’s cybersecurity maturity.
- Risk Prioritization: Assess and prioritize risks to guide targeted improvements and resource allocation.
Strategic Roadmap Development:
- Actionable Recommendations: Provide clear and practical recommendations to address identified gaps and enhance your cybersecurity maturity.
- Implementation Planning: Develop a strategic roadmap outlining the steps, resources, and timelines needed to achieve desired maturity levels.
Benchmarking and Best Practices:
- Industry Benchmarking: Compare your cybersecurity maturity against industry peers and best practices to understand your competitive standing.
- Adoption of Best Practices: Integrate industry best practices into your cybersecurity strategy to drive continuous improvement and maturity advancement.
Training and Awareness:
- Employee Training Programs: Develop and deliver training programs tailored to enhance the cybersecurity knowledge and skills of your workforce.
- Awareness Campaigns: Launch initiatives to promote a culture of cybersecurity awareness and continuous improvement within your organization.
Reporting and Documentation:
- Detailed Assessment Reports: Provide comprehensive reports detailing your current cybersecurity maturity level, identified gaps, and recommended actions.
- Executive Summaries: Offer high-level summaries for senior management to facilitate informed decision-making and strategic planning.
Continuous Improvement:
- Ongoing Assessments: Schedule regular maturity assessments to monitor progress, adapt to evolving threats, and ensure sustained cybersecurity improvements.
- Feedback Mechanisms: Implement feedback loops to refine and enhance your cybersecurity practices based on assessment outcomes and emerging best practices.

Enhanced Security Posture:
- Proactive Improvement: Identify and address weaknesses in your cybersecurity practices, advancing your security posture and reducing vulnerability to cyber threats.
- Comprehensive Protection: Implement mature cybersecurity processes and technologies that provide robust protection for your critical assets and data.
Strategic Alignment:
- Business-Driven Security: Align your cybersecurity strategy with your organization’s business objectives, ensuring that security initiatives support and enhance overall business goals.
- Resource Optimization: Allocate resources effectively by prioritizing initiatives that have the most significant impact on your cybersecurity maturity and business operations.
Regulatory Compliance:
- Meet Legal Requirements: Ensure compliance with relevant data protection and cybersecurity regulations, avoiding penalties and legal repercussions associated with non-compliance.
- Audit Readiness: Prepare for regulatory audits and assessments with thorough documentation and evidence of mature cybersecurity practices.
Risk Mitigation:
- Reduced Risk Exposure: Minimize the likelihood and impact of cyber incidents through effective risk management and mature security controls.
- Business Continuity: Ensure uninterrupted operations with robust incident response and disaster recovery plans integrated into your mature cybersecurity framework.
Increased Customer Trust:
- Build Credibility: Demonstrate your commitment to cybersecurity by showcasing mature and effective security practices, fostering trust with customers, partners, and stakeholders.
- Competitive Advantage: Differentiate your organization from competitors by highlighting your advanced cybersecurity maturity and proactive risk management approach.
Continuous Improvement:
- Adaptive Security: Establish a framework for continuous improvement, enabling your organization to adapt to evolving cyber threats and business needs.
- Sustainable Practices: Maintain a resilient and robust cybersecurity posture through ongoing monitoring, assessment, and enhancement of your security measures.
Cost Savings:
- Reduced Remediation Costs: Addressing security gaps early in the maturity lifecycle is more cost-effective than dealing with breaches and incidents post-occurrence.
- Efficiency Gains: Achieve cost savings by optimizing security processes, reducing redundancies, and leveraging mature cybersecurity practices for operational efficiency.
Use Cases:
Financial Institutions:
- Enhance cybersecurity maturity to protect sensitive financial data, ensure compliance with industry regulations, and maintain customer trust.
Healthcare Organizations:
- Safeguard patient information and medical records by advancing cybersecurity practices to comply with healthcare data protection regulations and standards.
Government Agencies:
- Secure classified and sensitive government data by elevating cybersecurity maturity, maintaining national security, and ensuring regulatory compliance.
E-Commerce Platforms:
- Protect customer data and transaction information by advancing cybersecurity practices, enhancing trust, and reducing the risk of data breaches.
Telecommunications Companies:
- Strengthen network security and customer data protection by improving cybersecurity maturity, ensuring reliable and trusted service delivery.
Educational Institutions:
- Safeguard academic records and personal information of students and staff by elevating cybersecurity practices to comply with data protection standards.
Manufacturing Firms:
- Protect intellectual property and operational technologies by advancing cybersecurity maturity, ensuring business continuity, and maintaining competitive advantage.
Retailers and Merchants:
- Secure point-of-sale (POS) systems and customer data by enhancing cybersecurity maturity, ensuring compliance with privacy laws, and maintaining customer trust.
