Threat Vulnerability & Risk Assessment Services
Threat Vulnerability & Risk Assessment Services
In today’s dynamic threat landscape, identifying and mitigating potential vulnerabilities is
essential for safeguarding your organization’s critical assets and ensuring business continuity. Our Threat Vulnerability & Risk Assessment Services provide a comprehensive analysis of your systems to uncover weaknesses, assess the risks associated with various threats, and implement
effective strategies to enhance your security posture.
Whether you’re aiming to protect sensitive data, comply with regulatory requirements, or prevent costly security breaches, our tailored assessments deliver the insights and solutions you need to stay ahead of cyber threats.
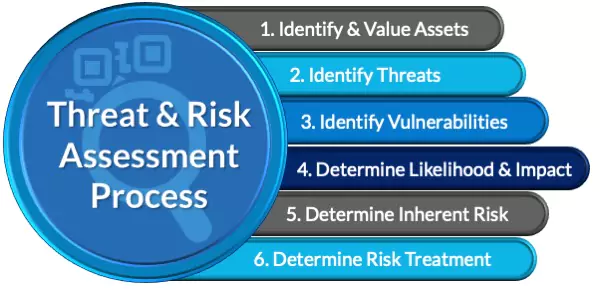
Our Threat Vulnerability & Risk Assessment Services are designed to systematically identify, evaluate, and prioritize vulnerabilities within your IT infrastructure. By analyzing potential threats and assessing the associated risks, we help you understand your organization’s security landscape and implement proactive measures to mitigate risks. Our approach combines advanced tools, expert analysis, and industry best practices to provide a clear and actionable roadmap for enhancing your cybersecurity defenses.
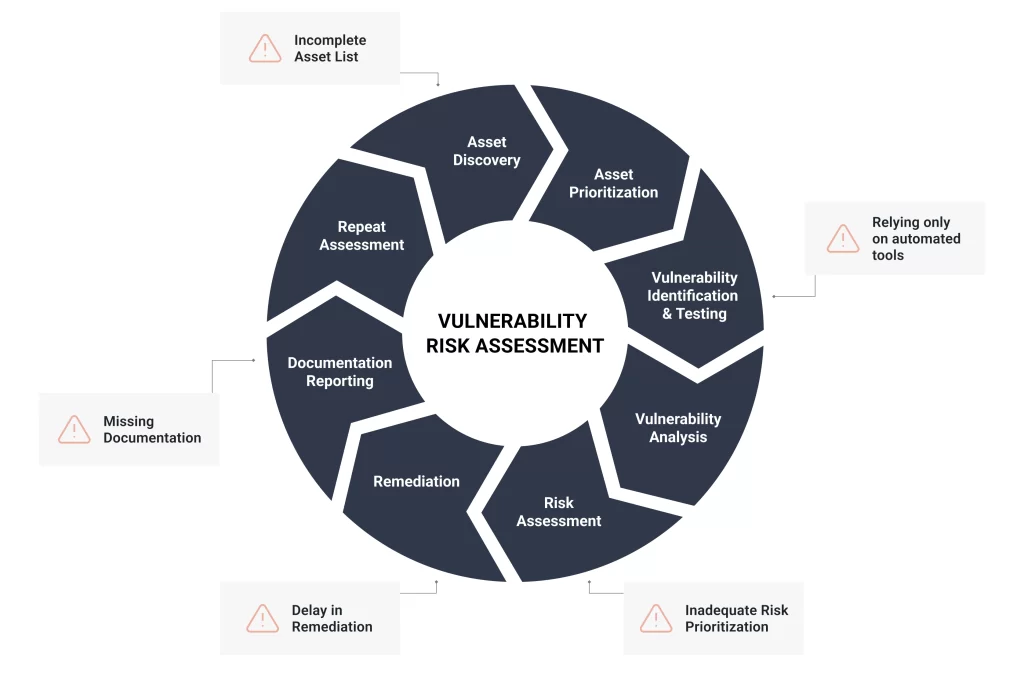
- Comprehensive Vulnerability Assessment:
- Automated Scanning: Utilize state-of-the-art automated tools to perform thorough scans of your network, applications, and systems to identify known vulnerabilities.
- Manual Testing: Conduct in-depth manual testing by experienced security professionals to uncover complex and hidden vulnerabilities that automated tools may miss.
- Configuration Review: Assess system and network configurations to ensure they adhere to security best practices and industry standards.
- Threat Analysis:
- Threat Identification: Identify potential threats that could exploit existing vulnerabilities, including malware, ransomware, insider threats, and advanced persistent threats (APTs).
- Threat Intelligence Integration: Leverage up-to-date threat intelligence to understand the latest attack vectors and tactics used by cybercriminals targeting your industry.
- Risk Assessment:
- Impact Analysis: Evaluate the potential impact of identified vulnerabilities and threats on your organization’s operations, data, and reputation.
- Likelihood Determination: Assess the probability of each threat exploiting a vulnerability based on current security measures and threat landscape.
- Risk Prioritization: Rank risks based on their severity and likelihood to prioritize remediation efforts effectively.
- Security Posture Evaluation:
- Current State Analysis: Examine your existing security controls and defenses to determine their effectiveness in mitigating identified risks.
- Benchmarking: Compare your security posture against industry standards and best practices to identify gaps and areas for improvement.
- Remediation Planning:
- Actionable Recommendations: Provide clear and practical recommendations to address identified vulnerabilities and reduce associated risks.
- Prioritization of Remediation Efforts: Help you prioritize remediation activities based on risk severity, resource availability, and business impact.
- Implementation Support: Offer guidance and support in implementing recommended security measures and improvements.
- Reporting and Documentation:
- Detailed Reports: Deliver comprehensive reports outlining findings, risk levels, and recommended actions to enhance your security posture.
- Executive Summaries: Provide high-level summaries for senior management to facilitate informed decision-making and strategic planning.
- Compliance Documentation: Assist in maintaining documentation required for regulatory compliance and security audits.
- Continuous Monitoring and Reassessment:
- Ongoing Risk Management: Establish continuous monitoring processes to detect and respond to new vulnerabilities and emerging threats.
- Periodic Reassessments: Schedule regular assessments to ensure your security measures remain effective and adapt to evolving cyber threats.
- Training and Awareness:
- Employee Training Programs: Educate your staff on cybersecurity best practices, threat awareness, and their role in maintaining a secure environment.
- Awareness Campaigns: Launch initiatives to promote a culture of security awareness and vigilance within your organization.
- Enhanced Security Posture:
- Proactive Threat Mitigation: Identify and address vulnerabilities before they can be exploited by malicious actors, reducing the risk of security breaches.
- Comprehensive Protection: Implement layered security measures that provide robust protection against a wide range of cyber threats.
- Regulatory Compliance:
- Meet Legal Requirements: Ensure compliance with relevant data protection and cybersecurity regulations, avoiding penalties and legal repercussions.
- Audit Readiness: Prepare for security audits and assessments with thorough documentation and evidence of risk management practices.
- Operational Efficiency:
- Streamlined Processes: Optimize security processes and workflows to enhance operational efficiency and reduce complexity.
- Resource Optimization: Allocate security resources effectively by focusing on high-priority risks and critical vulnerabilities.
- Risk Mitigation:
- Reduced Risk Exposure: Minimize the likelihood and impact of cyber incidents through effective risk management and mitigation strategies.
- Business Continuity: Ensure uninterrupted operations with robust incident response and disaster recovery plans in place.
- Increased Customer Trust:
- Build Credibility: Demonstrate your commitment to protecting customer data and maintaining a secure environment, fostering trust and loyalty.
- Competitive Advantage: Differentiate your organization from competitors by showcasing your proactive approach to cybersecurity and risk management.
- Cost Savings:
- Reduced Remediation Costs: Address vulnerabilities early in the development lifecycle, avoiding the high costs associated with post-incident remediation.
- Prevented Downtime: Minimize the financial impact of security breaches and downtime caused by unresolved vulnerabilities.
Use Cases:
- Financial Institutions:
- Protect sensitive financial data and transactions, ensuring compliance with industry-specific cybersecurity requirements.
- Healthcare Organizations:
- Safeguard patient information and medical records, complying with healthcare data protection regulations and standards.
- Government Agencies:
- Secure classified and sensitive government data, maintaining national security and public trust.
- E-Commerce Platforms:
- Ensure the security of customer data and transaction information, enhancing trust and reducing the risk of data breaches.
- Telecommunications Companies:
- Protect communication networks and customer data, maintaining reliable and trusted service delivery.
- Educational Institutions:
- Safeguard academic records and personal information of students and staff, ensuring compliance with data protection standards.
- Manufacturing Firms:
- Protect intellectual property and operational technologies from cyber threats, ensuring business continuity and competitive advantage.
- Retailers and Merchants:
- Secure point-of-sale (POS) systems and customer data to prevent data breaches and maintain compliance with privacy laws.
