Essential Eight
Essential Eight
Our Essential Eight Compliance Services are meticulously designed to help organizations implement and maintain the baseline security measures recommended by the Australian Cyber Security Centre (ACSC). The Essential Eight is a prioritized list of strategies aimed at mitigating cybersecurity incidents and enhancing your organization’s resilience against cyber threats. By aligning your security practices with the Essential Eight, we ensure that your organization establishes a strong foundational defense, reduces vulnerability, and maintains compliance with national cybersecurity standards.
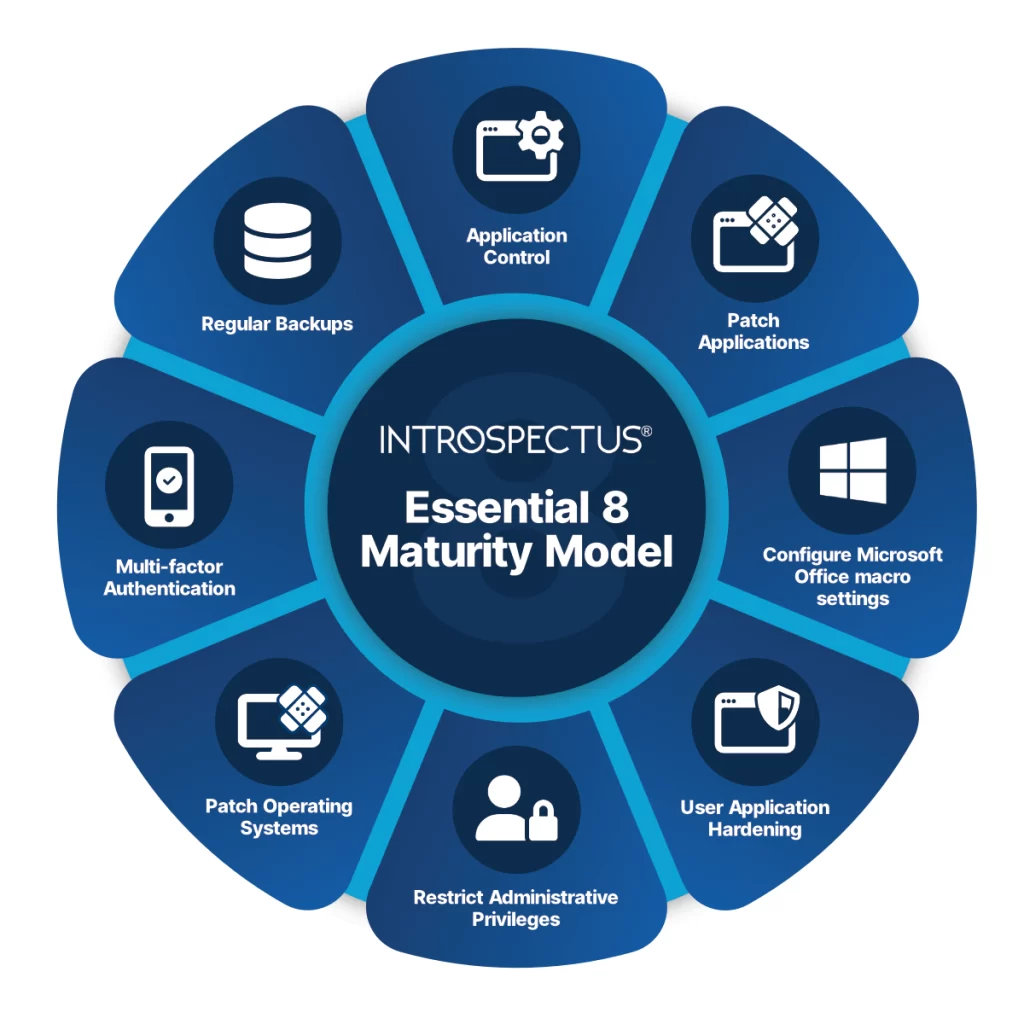
Key Features:
- Comprehensive Security Assessment:
- Gap Analysis: Evaluate the current security posture.
- Risk Assessment: Identify potential threats and vulnerabilities.
- Compliance Audits: Ensure effective implementation of security controls.
- Framework Implementation:
- Application Whitelisting: Prevent unauthorized applications from running.
- Patch Management: Ensure timely updates to applications.
- Macro Settings Configuration: Control macro usage in Microsoft Office to prevent malicious execution.
- User Application Hardening: Disable unnecessary features to reduce risks.
- Administrative Privilege Restrictions: Limit access to authorized personnel only.
- Operating System Patching: Keep operating systems up to date.
- Multi-Factor Authentication (MFA): Add extra security layers for sensitive data access.
- Daily Data Backups: Ensure recovery of important data after incidents.
- Training and Awareness Programs:
- Employee Training: Educate staff on cybersecurity best practices.
- Awareness Campaigns: Foster a security-conscious culture within the organization.
- Continuous Monitoring and Improvement:
- Real-Time Monitoring: Detect and respond to security threats promptly.
- Regular Reviews: Adapt security practices to evolving threats.
- Performance Metrics: Measure the effectiveness of security implementations.
- Incident Response and Management:
- Incident Response Planning: Develop effective strategies for incident management.
- Forensic Analysis: Investigate security incidents to prevent recurrence.
- Disaster Recovery Planning: Ensure business continuity during major incidents.
- Technology Integration:
- Security Tools Implementation: Enhance security infrastructure with advanced tools.
- Automation and Reporting: Streamline compliance management through automated solutions.
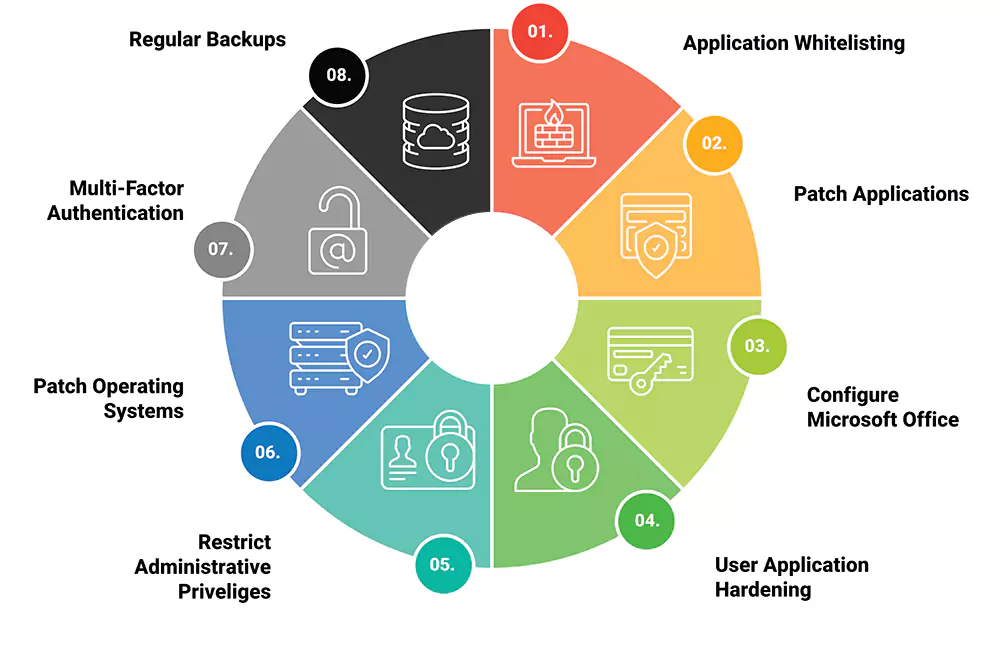
Benefits:
- Ensure regulatory compliance and avoid penalties.
- Protect sensitive data and enhance overall security posture.
- Improve operational efficiency and reduce risks.
- Build customer trust and gain a competitive advantage.
- Foster continuous improvement and achieve cost savings.

Our Essential Eight Compliance Services help organizations implement the Australian Cyber Security Centre’s (ACSC) security measures. Key offerings include security assessments, implementation of Essential Eight strategies, ongoing training, and incident response planning. These services enhance security, ensure compliance, and build customer trust while minimizing risks across various sectors.
Use Cases:
- Financial Services:
- Protect sensitive financial data and transactions, ensuring compliance with industry-specific information security requirements.
- Healthcare Organizations:
- Safeguard patient information and medical records, complying with healthcare data protection regulations and standards.
- Government Agencies:
- Secure classified and sensitive government data, maintaining national security and public trust.
- E-Commerce Platforms:
- Ensure the security of customer data and transaction information, enhancing trust and reducing the risk of data breaches.
- Telecommunications Companies:
- Secure communication networks and customer data, maintaining reliable and trusted service delivery.
- Educational Institutions:
- Protect academic records and personal information of students and staff, ensuring compliance with data protection standards.
